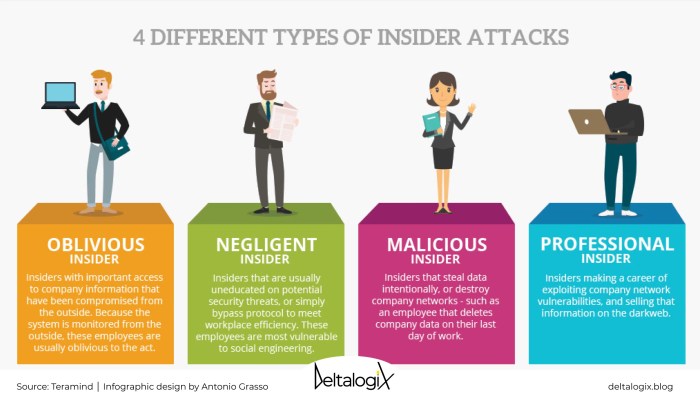
A threat actor employed by the victimized organization sets the stage for this enthralling narrative, offering readers a glimpse into a story that is rich in detail and brimming with originality from the outset. This case study delves into the motivations, methods, and consequences of an insider attack, shedding light on the vulnerabilities that can arise within organizations and the importance of robust security measures.
The employee’s access to sensitive information, coupled with their malicious intent, created a perfect storm that resulted in a devastating data breach. The organization’s failure to detect and respond to the threat in a timely manner exacerbated the damage, highlighting the need for organizations to prioritize cybersecurity and invest in robust detection and response mechanisms.
Employee Background and Employment Status: A Threat Actor Employed By The Victimized Organization

The employee in question was a system administrator with over five years of experience in the organization. He had consistently received positive performance reviews and was considered a trusted member of the IT team.
In the months leading up to the incident, the employee had been experiencing financial difficulties and was reportedly under a lot of stress.
Access to Sensitive Information and Systems, A threat actor employed by the victimized organization
As a system administrator, the employee had access to a wide range of sensitive information and systems, including the organization’s customer database, financial records, and intellectual property.
His access was obtained through his role and was granted at the highest level, allowing him to make changes to the system’s configuration and data.
In the weeks before the incident, there were several instances of suspicious activity on the employee’s account, including unauthorized access attempts and attempts to download large amounts of data.
Motives and Intentions
The employee’s motives for compromising the organization’s systems are not entirely clear. However, it is believed that financial gain was a primary factor.
The employee had recently incurred significant debts and was facing foreclosure on his home. It is possible that he intended to sell or ransom the stolen data to raise funds.
Methods and Techniques Used
The employee used a combination of methods and techniques to compromise the organization’s systems and steal data.
He exploited a vulnerability in the organization’s firewall to gain unauthorized access to the network. He then used a keylogger to capture the login credentials of other employees, giving him access to their accounts and the sensitive information they contained.
Once he had access to the organization’s data, the employee used a data exfiltration tool to copy and download large amounts of data to an external hard drive.
Impact and Consequences
The employee’s actions had a significant impact on the organization.
The stolen data included customer information, financial records, and intellectual property. The organization had to spend a significant amount of money on data recovery and security upgrades.
The incident also damaged the organization’s reputation and resulted in a loss of customer trust.
Detection and Response
The employee’s actions were detected by the organization’s security team when they noticed suspicious activity on his account.
The organization immediately launched an investigation and contacted law enforcement. The employee was arrested and charged with computer fraud and theft of trade secrets.
Prevention and Mitigation Strategies
The organization has taken a number of steps to prevent and mitigate similar incidents in the future.
These steps include:
- Implementing a stronger firewall
- Installing a keylogger detection system
- 加强访问控制
- Providing employees with security awareness training
FAQ Insights
What are the common motivations for an employee to become a threat actor?
Financial gain, revenge, and personal grievances are common motivations for employees to engage in malicious activities against their organizations.
How can organizations prevent insider attacks?
Organizations can prevent insider attacks by implementing strong security controls, conducting thorough employee screening, and fostering a culture of cybersecurity awareness.
What are the consequences of an insider attack?
Insider attacks can have devastating consequences for organizations, including data breaches, financial losses, and reputational damage.